The Power of Agile Network Visibility

Product Overview
Niagara Networks™ is a Silicon Valley-based company that pioneers the Open Visibility Platform™ to bring desperately needed agility to network security. Niagara Networks provides high-performance, high-reliability network visibility and traffic delivery solutions for the world’s most demanding service provider and enterprise environments. Niagara Networks solutions are installed in the world’s most prominent networks, empowering Security and Network Operations Centers (SOC/NOC) with end-to-end visibility and actionable traffic intelligence across physical and virtual networks.
As a former division of Interface Masters, Niagara Networks provides all the building blocks for an advanced Visibility Adaptation Layer at all data rates up to 100Gb, including advanced packet brokers, bypass switches, network TAPs, and unified management and orchestration software that serves as a single pane of glass to ease configuration and provisioning of the visibility infrastructure. Thanks to its integrated in-house capabilities and tailor-made development cycle, Niagara Networks are agile in responding to market trends and in meeting the customized needs in the ever-changing network security market.
Packet data is an incredibly sophisticated area that any SOC and NOC massively use to identify security threats – Niagara Networks’ visibility solutions collect, inspect, and deliver the right packet data to threat detection/prevention tools. Niagara Networks’ award-winning Open Visibility Platform™ is designed to be open, exposing numerous points for technological integration and extensibility, and offers organizations the agility to host any virtualized security applications and monitoring tools.
- Network Visibility Orchestration
- Open Visibility Platform
- Inline Bypass Switches
- Network Intelligence
- Network Packet Broker
- Network TAP
- CloudRay - Cloud Intelligence Platform
- CloudRay - virtual TAP
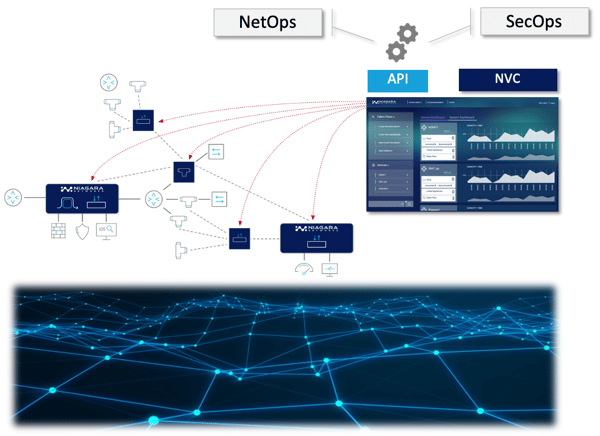
The pro-active visibility management mechanism should address the following three primary concerns:
- Enable a comprehensive 360° network visibility (on your visibility layer)
- Enable simple and intuitive configuration and provisioning of the visibility infrastructure as an intelligent cross connect
- Empower NetOps and SecOps to serve business agility enablement and maximum security posture
What this means is that now organizations have the freedom to choose, and not be tied to offerings of a particular vendor. Furthermore, swapping an existing solution for a new one that you want to add no longer needs to be a lengthy, dragged out process. This freedom will also promote innovation as there is now a place to deploy new things.
NetOps and SecOps Challenges
The ability to deploy a security—or even a networking—solution in the network has been a long, complicated process. Much has stood in the way of progress, making the ability to add or change solutions difficult and causing this area to be one of the least agile in the design and implementation process of operational teams.
- Security threats and networks are continuously changing.
- Security solutions are constantly advancing.
- Difficulty in deploying new solutions on the network or changing existing ones.
A Network Bypass Switch ensures failover or fail-safe capabilities for an inline networking device or a network security tool such as a firewall, NGFW, IDS/IPS, WAF, DDOS and many other flavours of threat detection platforms. If the network or security appliance fails or needs to be taken off-line for whatever reason, its traffic is automatically rerouted, ensuring uninterrupted traffic flow on the network.
What is a Network Bypass Switch?
Redundancy is essential and highly critical aspect for any network that needs to operate all the time. Bypass Switches sometimes also referred to as a bypass tap, the network bypass switch, is a special type of active tap. It is used to connect a network segment at a specific network access point (TAP) where there is an active, inline device (such as a security tool that is there for inspection and monitoring purposes).
Functionally, it can reroute traffic automatically by monitoring the tool’s health or can manually be made to redirect traffic (such as when disconnecting the monitoring tool for maintenance or other motives). Since the inline network devices are essential to the overall functioning of the enterprise network – any issue with them can critically effect network performance.
Each network device that is placed inline is a potential single point of failure in the computer network. If the device should experience even the shortest period of system hang-up or failure (that takes time for a reboot or any kind of troubleshooting), then traffic flow will be discontinued. Even for maintenance or replacement purposes, disconnecting the device will interrupt normal traffic flow at that point.
Any dropped data packet is a potential cause of error or inaccuracy in the processes and applications that depend on receiving those data packets. Thus, the network bypass switch – that can circumvent any and all interruptions at that critical AP or network link – is an essential element of the network infrastructure. The network bypass switch eliminates this point of failure by redirecting the network data traffic to bypass around the network device at that point, whenever that device is incapable of processing or passing the traffic.
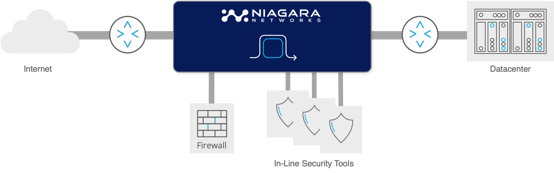
In case the bypass switch itself is somehow compromised, it contains a relay switch that is designed to close and go to 'bypass mode' and allow the traffic to seamlessly flow through its cable to maintain an uninterrupted and open link with the rest of the network. This is especially important with regards to security devices that need to continuously defend the network against malevolent attacks and security breaches.
Click here to view vendor product page>>
The mainstay of Network Packet Brokers (NPB), has always been ‘getting the right traffic to the right tool’. With the network’s traffic as its inputs, the NPB is able to replicate, aggregate, filter and load balance the traffic, to provide SecOps and NetOps with visibility that they need into the network. Intelligent traffic processing is required in order to increase the efficiency of the tools used by SecOps and NetOps and to address the growing sophistication in needs of Security Solutions.
Niagara’s Network Intelligence (NI) solution offers various advanced traffic processing capabilities that significantly extend the envelope of your network visibility and security visibility layer.
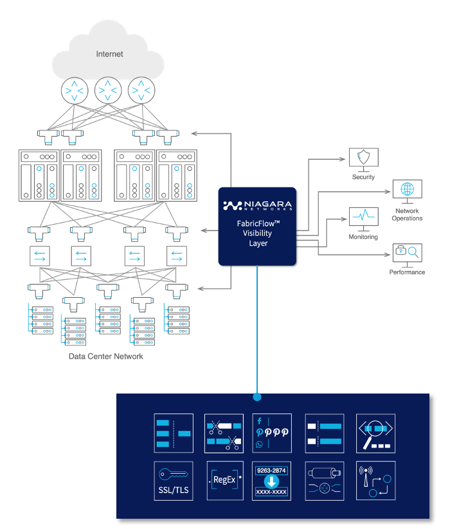
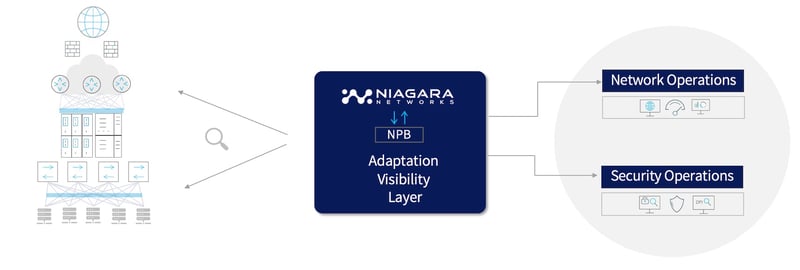
Niagara's Packet Brokers deliver access to network data to NetOps & SecOps to enable detection, investigation and response to threats in real-time. Our NPB solutions are empowered by comprehensive Technology Alliance Program with world-class technology leaders and deployed in the world's most prominent networks.
What Exactly Does a Network Packet Broker Do?
Niagara’s NPB advanced solutions perform a range of crucial functionalities for all types of networks, even those with extremely complex architectures and that are resource-intensive including:
- Total Network Visibility - Identifying known, suspicious, and unknown traffic passing through the network
- Network robustness - Ensuring data loss prevention and advanced filtering, as well as high availability, stripping, and other special-purpose packet capabilities. Including complex Regular Expression(REGEX) filtering and headers stripping for filtered traffic which inspection tools can process and analyze
- Network management - Not just knowing how to monitor network traffic, but also knowing what to do with each type of traffic: where to pass known (authorized) data types, and how to handle suspicious and unknown traffic to simplify APM and NPM analytics and reporting
- Advanced network security - streamline security analysis and advanced threat detection and prevention
In their role as data analyzers, Niagara’s Packet Brokers can also handle deduplication of redundant (duplicate) packets before they reach analysis or security tools within the network, that are passed along by multiple TAPs forwarding their data traffic. The NPBs will eliminate those duplicates and make sure network tools do not waste resources on handling redundant data.
Click here to view vendor product page>>
What is a Network TAP (Terminal Access Point)?A network TAP is an external network device that creates a “copy” of the traffic for use by various monitoring devices. It allows traffic mirroring and is an intricate part of an organization's network stack. The network TAP device is introduced at a point in the path of the network that is felt should be observed, so that it can copy data packets and send them to a monitoring device. The network designer will decide where the significant points for the network TAPs should be placed in the network infrastructure, based on the reason for network interface observation: data gathering, analysis, general network monitoring (such as for saturation and latency), or more critical, such as for intrusion detection, etc.
Tapping creates a copy of the traffic, the network TAP device does not modify the network traffic in any way. The traffic on the network is unaffected by the act of tapping and monitoring. Since the monitoring is performed on a copy of the traffic by a device external to the network, via a TAP network adapter, this deployment is often referred to as 'out of band'.
A TAP acts as an ‘unobtrusive observer’ of the traffic, and just feeds a copy of the data to the attached device, often a monitoring tool or a TAP aggregation device (Packet Broker). This provides full network visibility at that point. At the same time, however, should the network TAP device or monitoring device fail, it will in no way affect the traffic or its flow and thus ensures that the network remains active and secure.
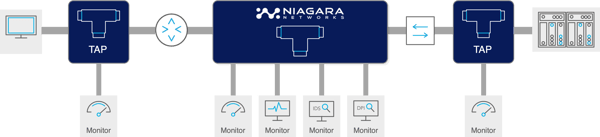
A network TAP device comes in both passive and active versions – each type having its own particular advantages for network monitoring in high density networks. Active TAP devices take part in the link negotiations and often provide additional functionality like TAP aggregation. In a copper network, TAPs must always be powered. Niagara's active network TAP devices provide fail-safe circuitry ensuring that traffic keeps flowing through the network when the power fails on the network TAP device. Another effective type of network TAP is the passive fiber TAP. Fiber optic TAPs are coiled into the optical fiber line and mirror all network traffic without introducing a point of failure and provide the secure access of network data in optical networks. Passive optical TAPs do not require any power and are therefore truly passive devices.
Click here to view vendor product page>>
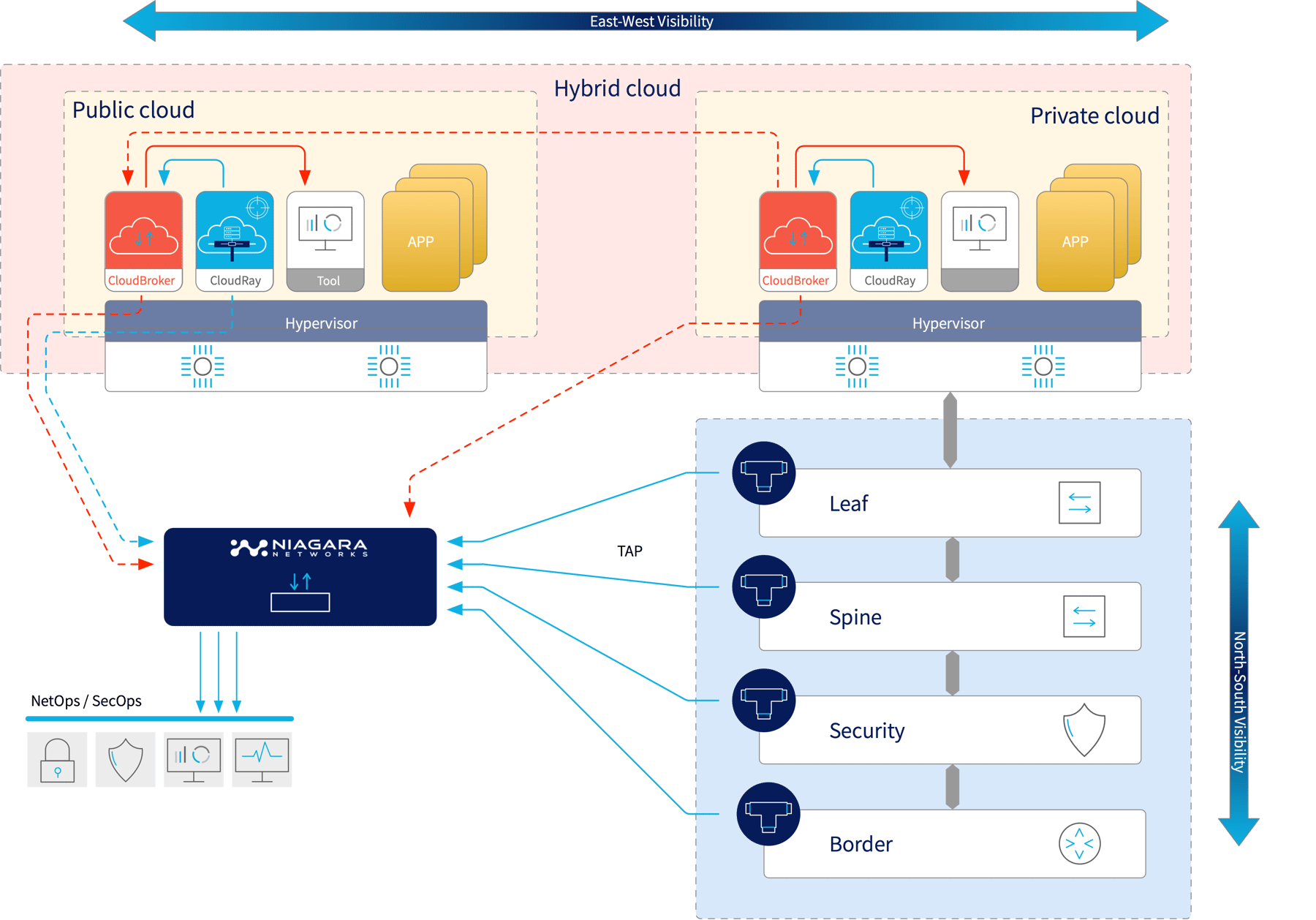
n today's fast-paced digital world, businesses are embracing the benefits of hybrid cloud environments. However, as these environments become more complex, it's essential to have a comprehensive view of network traffic across your entire infrastructure - on-prem, private cloud, and public cloud environments. That's where cloud packet brokers come in. A cloud packet broker is a virtual networking Cloud Intelligence Platform (CIP) that aggregates, processes, filters network packets, and ingests intelligent metadata, allowing you to see the data and metadata that matters most - specifically, in cloud-native environments. With the help of cloud packet brokers, you can achieve hybrid cloud visibility, providing you with critical insights into network performance observability, security, and compliance across on-prem, private cloud, and public clouds.
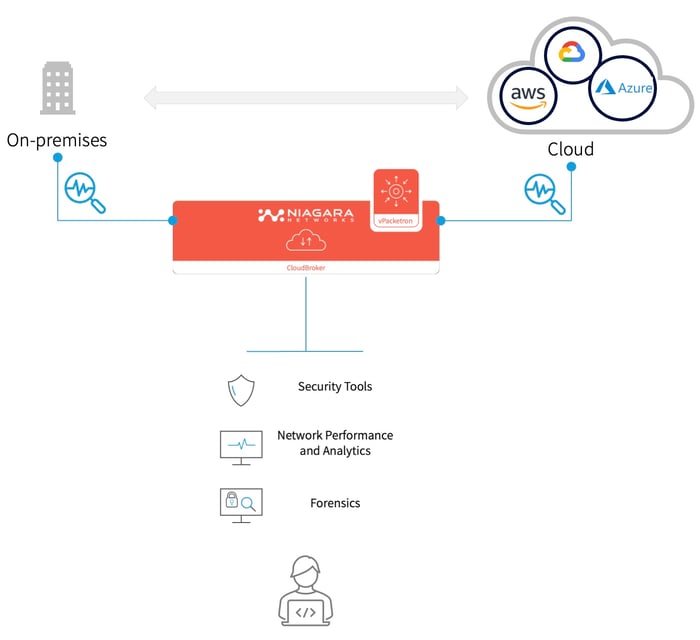
Multi-purpose solution for East-West and North-South Deployments – combining physical and virtual infrastructure
Click here to view vendor product page>>
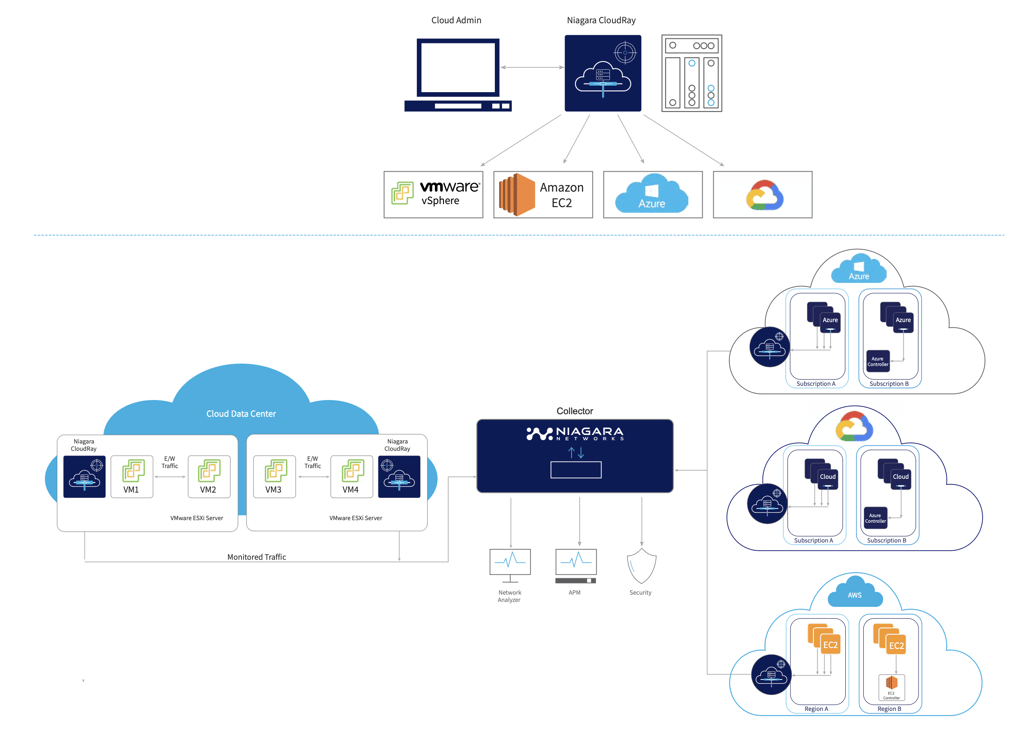
With increasing transition to data center and cloud based environments, IT teams find it challenging to use traditional monitoring tools for traffic visibility. Physical taps are unsuitable for virtual environments since they cannot monitor East-West and inter-VM traffic. Moreover, they cannot track VMs when moved across hypervisors. Niagara Networks’ CloudRay-vTAP is a software solution that addresses these challenges, providing complete visibility of VM traffic in virtual computing environments, be it Private, Public or Hybrid clouds.
CloudRay Key Benefits
- Enables Visibility-as-a-Service (VaaS) - agile deployments in cloud-based architectures
- Supports Private, Public, and Hybrid Cloud visibility requirements
- Tenant based tunnels, facilitating isolation, privacy, and compliance
- Blindspot removal with total visibility of East-West, inter-VM, and blade server mid-plane traffic
- Reduced network bandwidth with multi-layer filtering for virtual network traffic optimization
- Enabling SLA compliance and comprehensive troubleshooting for NOC teams
- One-touch installation enabling bulk deployments with operational simplicity
- Centralized control with a dashboard for orchestration and monitoring
- Complements existing physical TAPs
Click here to view vendor product page>>
Target Industries
Government
Telecoms
Oil & Gas
Hospitality
Financial
Education
Niagara Networks Distribution Team
If you are interested in Niagara Networks products and solutions, or would like to find out more, contact our team.
